Ask any IT person who they believe is capable of wreaking the most havoc on a corporate network; a skilled hacker or a well-intentioned but clueless employee - chances are excellent they'll pick the latter.
Keeping people out of a network is much easier than managing the activities of people who legitimately have access to the network and a company's critical data. On any given day one disgruntled employee might indulge in a little corporate espionage, another may be carelessly installing spyware in the guise of amusing screensavers, or games that harbour keyloggers that came from 'a friend' in an email.
Then again you'll find someone is responding to a phishing email with the user name and password she uses to log onto the network, while someone else is downloading heaps of data onto their laptop to work on over the weekend, and yet another has just plugged the ethernet cord into his virus-laden portable device. Any of these activities obviously endanger the security of critical data.
Creating and enforcing a use and misuse policy controlling what users - including top executives, the head of IT and the database manager - do with data is critical. Policies must also be reviewed regularly to ensure they reflect the current regulatory climate and any new knowledge or concerns that may have cropped up. This article outlines best practice policies concerning computer use and misuse, as well as the technical solutions that support those policies.
Creating a computer use policy
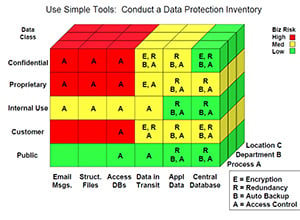
Conducting a full audit of the entire system is a vital first step in any data-driven security project. You must identify all the points and places where sensitive data is processed, transmitted and stored as you can't protect data if you don't know where it is. Audits typically reveal sensitive personal data tucked away in places that you'd never expect to find it, unprotected in portable devices, storage media, applications and databases across the network.
Click for larger image
Once you know where the data goes and lives, you can develop a plan to protect it and the systems it resides in - a plan that is very specific to your business needs. The plan should address such issues as data retention and disposal, user access, permitted and prohibited activities, encryption and auditing and enforcement.
It is best to develop the plan and its ensuing policies in tandem with representatives from departments throughout the company. Each of your employees is a stakeholder in security and should feel as if he or she is a valued participant in protecting company data. People's concerns about data security interfering with business processes and productivity must be respected and taken into account when developing security policies and processes. If you don't, then staff will create workarounds.
You will likely want to develop the policy with the assistance of your legal department. Smaller companies without this resource may find it useful to hire a lawyer to review the policy to ensure all bases are covered. But don't let the policy be turned into a long droning document stuffed with legalese. If people can't understand the policy they can't abide by it.
Contents of the policy
Among the subjects you should address in the policy are:
- Approved activities: Clearly state that all equipment and data belongs to the company and is not to be copied, shared, or accessed without permission. You may then go on to list other activities that are permitted. Are chat clients and personal web email allowed? Can users conduct personal business on their computers/online during breaks? Can users connect to the corporate network via public wireless networks when they're out of the office? Can data be downloaded into portable devices or storage media so that users can work at home or on the road? If data can be shared with approved third parties, what procedures are in place to protect the data?
- Prohibited activities: Your policies on data transfer / downloads, storage on portable devices, sharing of passwords and log-in information, sharing personal data (customers or personnel) with others, installing software onto the desktop or web browser, email policies regarding attachments. If users are not allowed to change settings on applications (such as change the security setting on their browsers, or deactivate programs on their desktops) state that policy here. You might also want to refer employees to your security policy for complete details on security policies and processes.
- Tampering: This falls under prohibited activities, but you may opt to have a separate section. It would stress that knowingly creating, executing, forwarding, or otherwise introducing computer code designed to damage, destroy, self-replicate, surreptitiously gather information, or otherwise impact or impede the performance of corporate communications assets including computers, data, storage or software is prohibited.
- Privacy and monitoring: Make sure users know that they have no expectations of privacy regarding any electronic communications and files received via, or stored on, 'their' computers and company-owned electronic devices. Let them know that the system is audited to ensure compliance with usage and security policies.
- Intellectual property and licensing: Rules regarding software use, copying and user installations of software.
- Disciplinary action: The consequences if computer use policies are violated, warnings, probation, suspension, termination. You may opt to state that any employee discovered intentionally breaking the policy for any reason will be dismissed.
Employees should sign the policy to acknowledge that they have read it in its entirety and will abide by it.
Enforcement and understanding
Far too often companies, government agencies and departments establish good strong data security policies, everyone signs off on those policies... and then does whatever they want to do.
The Ponemon Institute, in its recent report 'Data Security Policies Are Not Enforced' found that more than half of the survey's respondents had copied confidential company information onto portable devices though more than 87 per cent also said that company policy forbids such practices. About 46 per cent said they routinely share passwords with colleagues, even though two-thirds of those respondents admitted that their company's security policies prohibit password sharing.
Simply devising policies isn't enough. Given the differing feelings that may be present about data security, policies and procedures should be automatically enforced by technology controls such as role-based access, data encryption and auditing tools to ensure that everyone is following the rules. And to protect data from misuse and / or exposure, even if the rules are broken.
But don't make your employees feel as if they are being mercilessly monitored continually by an overzealous big brother. Let them know that effective security systems benefit all members of the company.
One of the most positive steps an enterprise can make is to institute ongoing security awareness training for employees. Ensure that all employees understand how to identify confidential information, the bottom-line business importance of protecting data and systems, how to choose and use passwords, acceptable use of system resources, email, and the company's security policies and procedures.
The best way to secure your data and systems is to team the right technological solutions, policies and processes with a strong culture of security, one in which employees are given the information and training that they need to protect data and have a clear understanding that defending data is central to the firm's and their own professional success.