Cloud computing is an evolving paradigm. It has accelerated the rapid globalisation and outsourced diffusion of hardware and software systems, drastically altering consumer’s perception of infrastructure architectures, software delivery and development models.
The cloud leverages software capabilities for agility, which is a somewhat different approach to the traditional data centre resource provisioning method. The components of a cloud service, particularly software-as-a-service (SaaS) applications, are made up of loosely coupled services. These software programs are often written by a large group of developers scattered around the globe.
The cloud has promoted an application economy, where cloud service providers (CSP) do not spend their time building software from the ground up. Instead, CSPs manufacture cloud applications, utilising billions of parts from global vendors through competitive sourcing.
Recent studies into the supply chain of cloud services have also shown that at least 80 per cent of a typical SaaS application is made up of assembled parts, with each component representing a different level of risk.
With 1.8 billion vulnerable open source components downloaded in 2015 and at least 26 per cent of the most common open source components having high-risk vulnerabilities (1), the risks of multi-cloud systems would seem to be ever-increasing.
Cloud risks are associated with the processes, procedures, and practices used to assure the integrity, security, resilience, and quality of cloud services. Due to its nebulous nature, assessing and managing cloud risks can pose a challenge since significant portions of the computing services are under the control of external cloud providers.
The cloud supply chain is a complex system of several organisations and processes involved in the delivery of a cloud service.
The cloud inherits the risk of its underlying architecture, e.g. the internet and web services, but introduces an extra layer of complexity. Also, uncertainty multiplies within the web of complexity involved in cloud service delivery, giving room for potential weak links to lurk around the supply chain.
Many of the typical cloud computing risks related to multi-tenancy, lack of transparency, performance and reliability issues, vendor lock-in, security and compliance concerns, were not evident under the traditional computing model. These risks increase with the on-demand, automated, and dynamic cloud, where customers and providers are rapidly changing, and data and services are regularly exposed to new threats.
The nested nature of the cloud and the myriad of interconnected service providers exacerbates the complexity of accountability, risk, and trust relations between the subscribers and CSP.
According to the 2017 Global Cybersecurity Assurance Report Card, cloud risk assessment is considered as one of the most significant enterprise security weaknesses worldwide (2). Cloud risk assessment is still in its infancy. Currently, and despite the very many discourses about cloud computing risks, there is no structured framework for assessing cloud risks, and neither is there a robust vocabulary about the elements of cloud risk.
Although, during the past decade, there has been an increasing amount of literature targeted at addressing cloud computing risks and how they can be mitigated, very little research has considered the inherent cloud supply chain as a source of these cloud risks.
Many of the current cloud risk assessment methods are based on the traditional IT risk assessment methods, which were developed in the days when firms hosted data in private data centres.
This traditional approach was designed to be periodic (yearly) on the assumption that systems do not change significantly over a short period, but their application to cloud computing has failed to cater to the complexity or pervasiveness of the dynamic and automated nature of systems.
The works of Alturkistani et al (3) and Drissi & Benhadou (4) present a cross-section of the recently developed cloud risk assessment models. Conversely, many of these models are not widely adopted, perhaps because they are not robust enough to address a wide range of cloud risks, particularly the security risks experienced by the CSPs.
How do we then approach the risk assessment of a cloud service?
We need to consider the supply chain, and how cloud supplier risks cascade into the overall risk of the cloud service. There are two primary approaches to supply chain risk management. The first centres on the focal company, while the second considers the performance of the members of the supply chain.
Cloud risk assessments, have hitherto followed the first approach, but seeing that this has failed to account for the vendors involved in the cloud delivery and their inherent risks, we can make a case to have all entities and components involved in the delivery of the cloud service included in the assessment.
This approach to risk assessment is not reliant on having a perfect knowledge of the supplier’s security controls, because, the transparency of the supply chain, i.e. the degree of visibility or information sharing among the members, varies with cloud deployments.
Also, the loose coupling between cloud components, supported by the free-market economy, has led to a regular update of cloud services, in a way that could complicate risk assessment. Notwithstanding, the focal CSP should, as part of the risk assessment of their cloud service, identify each component and its suppliers.
Using the information available to them about their supplier’s approach to cloud security and the evidence of security control, CSPs should evaluate and objectively compare the security performance of their suppliers, by applying quantitative and effective metrics that are based on a standard vocabulary. The result of this exercise is that the CSP is then able to identify which of its suppliers pose the most significant threat to the cloud service and focus its efforts in that direction to minimise the exposure.
In line with the suggested supply-chain approach, we are in the process of developing the Cloud Supply Chain Cyber Risk Assessment (CSCCRA) model (5). The CSCCRA is proposed as a quantitative risk assessment model that is supported by a supply chain mapping tool and a cloud security supplier assessment (CSSA) tool. It builds on existing risk assessment standards and guidance documents such as ISO 27005, ISO 31000, NIST 800-30v1, and the FAIR risk assessment.
The CSCCRA will be targeted at cloud provider risk assessment, and will involve identifying the components of a cloud service and corresponding supplier, and presenting this information as a cloud supply chain map or data flow diagram.
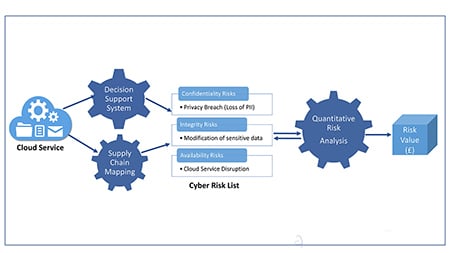
Diagram: Andrew Martin/Steve New/Olusa Akinrolabu
The CSSA is a supplier rating service (SRS), that uses a multi-criteria decision-making method to rank suppliers based on nine security target dimensions, which are the results of a just-concluded Delphi study. Some of the target dimensions include availability of service, data security controls, and maturity of operational security etc., each of which includes several contributing elements.
The CSSA is designed to bring transparency to the security risk rating exercise of cloud suppliers, providing a quantitative measurement of security performance across the chain, identifying the inherent risks and comparing suppliers based on their cybersecurity posture.
The risk analysis phase of the CSCCRA will present the value of cloud risk in monetary terms to provide more information to facilitate an efficient decision-making process. Because, while the cause of most cybersecurity incidents is due to technology failure, its effect is mainly business, involving loss of customers, financial fines, legal costs, remediation cost, and loss of reputation.
This approach to cloud risk assessment is based on the current knowledge of the CSP about its supply chain; a knowledge that improves with each assessment. The CSCCRA aims to aggregate the risk of the cloud service, due to its systematic breakdown of cloud risk elements. Seeing that supply chain security is an incredibly complex problem and that the strength of the cloud supply chain depends on the strength of its weakest member, our approach of finding the weak links in a cloud supply chain is expected to yield positive results.
While it might not guarantee that the cloud service will be attack-proof, its systematic and structured approach to identifying security risks within the supply chain and ranking them in the order of CSP-concern can help to promote cost-effective risk mitigation and optimal risk prioritisation.
Conclusion
Conducting a comprehensive security risk assessment is one of the ways CSPs can address the supposed culture of lack of responsibility and accountability among members of its supply chain. To implement the supply-chain aware cloud risk assessment described in this article, CSPs must address the dynamism of their supply chain, and the lack of visibility of supplier security controls.
There are several advantages of this supply-chain approach to cloud risk assessment, one of which is the understanding CSPs gain from the breakdown of their cloud service into its component elements.
The process of supply chain mapping and supplier ratings enables the CSP to step back cognitively from their usual approach to risk assessment, to re-assess their knowledge of the cloud service, the criticality of its components and prioritise specific aspects of its delivery, e.g. security.
Also, this new approach helps CSPs to influence their supply chain where appropriate and can lead to the formation of strong alliances among supply chain members, ultimately leading to a more secure cloud service.

















