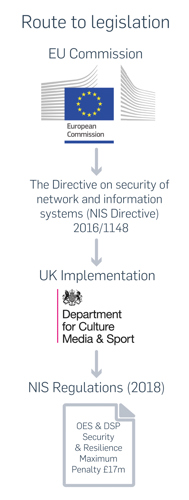
General Data Protection Regulation (GDPR) has overshadowed the introduction of the Network and Information Systems (NIS) Directive, even though the regulations came into force earlier, on the 10th May 2018.
The NIS Directive implements the first European Union (EU) wide rules for cyber security. The Directive affects operators of services deemed to be vital to the economic and societal activities of the EU, usually known as critical infrastructure, and includes other relevant digital service providers.
The NIS Directive will concentrate board members’ attention on cyber security, with a potential maximum £17 million penalty (not the anticipated GDPR equivalent four per cent of global turnover).
The resilience of critical services highlights the requirement to secure not only information systems, but the technologies that are relied upon to operate essential services; known as cyber physical systems, industrial control systems (ICS) or operational technology (OT). Their disruption or failure can impact many people and cost millions, with potentially severe consequences.
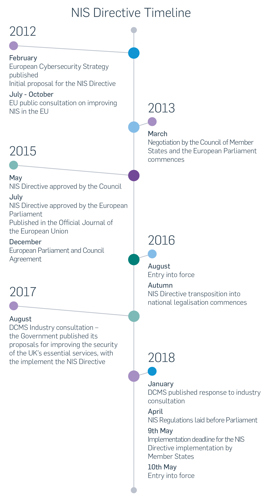
The recent watershed attack (HatMan) late last year targeted a Schneider Electric Triconex safety shutdown system in the Middle East (widely reported to be the Saudi Arabian oil and gas sector), stopping critical infrastructure plant operations. This incident illustrates the increasing capability and intent to attack specific critical infrastructure, and the motivation to compromise safety systems.
Recent destructive attacks include NotPetya, which masqueraded as ransomware. Reckitt Benckiser, the consumer products manufacturer (brands include Dettol, Nurofen and Durex) predicted £100 million losses. The transport and logistics company Maersk declared losses exceeding $300 million. Fedex estimated losses to be more than $500 million.
The pharmaceutical company Merck anticipated losses to exceed $600 million and needed to borrow paediatric vaccine from US government contingency stocks to meet demand, following manufacturing disruption.
Black Energy and Industroyer / CrashOverride attacks both targeted the Ukrainian power grid. The WannaCry ransomware affected the NHS, manufacturing plants, telecoms, transport and energy organisations globally. These highlight the necessity for proportionate risk-based cyber security and more importantly, operational resilience.
The UK implementation has significant implications for the operators of essential services (OES), relevant digital service providers (DSP) and competent authorities (CAs).
Background
The NIS Directive forms part of the EU Digital Market Strategy, which aims to make better use of digital opportunities for people and business and enhance Europe’s position as a world leader in the digital economy.
Digitisation has fundamentally changed entire economic sectors. Cyberspace is now regarded as the backbone of digital society and economic growth. However, cyber security incidents are increasing at an alarming rate and may disrupt the supply of essential services, and undermine trust in digital services and products.
The Directive’s intent is to improve the EU’s preparedness for a cyber attack, recognising that reliability and security of network and information systems, and the essential services they facilitate, are vital to society.
The UK Network and Information Systems Regulation (2018) apply to essential services; energy, water supply, healthcare, transport and key digital infrastructure. The UK implementation excludes nuclear, banking and financial sectors. Digital service providers with 50 or more staff and / or a turnover of €10 million will have similar, but less onerous requirements.
Approach
The directive seeks to increase security and resilience across the EU with a layered approach, focused at the member state, which includes setting the national strategy and facilitating collaboration between member states and OES.
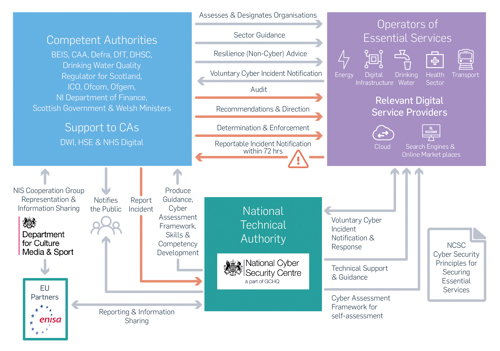
Notification obligations seek to promote cooperation, communications and knowledge, and assist in tackling cross-border threats. ENISA, the European Union Agency for Network and Information Security, will have a mandate under the proposed EU Cybersecurity Act to support member states in their implementation of the NIS Directive.
Devolved administrations and lead government departments will have responsibility as competent authorities (CAs), along with existing regulators, to manage specific industry sectors.
The Department for Digital, Culture, Media and Sport’s (DCMS) industry consultation response set the criteria for identifying OES. The consultation outcome clarified the identification of essential services, limitations on penalties, the roles of CAs to regulate specific sectors, the expectations on operators in the initial year, and the definition of relevant digital service providers (RDSP); defined as cloud services, online marketplaces and search engines.
Operators of essential services will have to implement ‘appropriate and proportionate security measures to manage risks.’ The Directive creates four high level objectives, which the UK has expanded into 14 high level security principles:
- Appropriate organisational structures, policies, and processes to understand, assess and manage security risks;
- Proportionate security measures to protect essential services and systems;
- Capabilities to ensure defences remain effective and detect cyber security events;
- Capabilities to minimise the impacts of a cyber security incident on the delivery of essential services including the restoration of those services where necessary.
National Cyber Security Centre’s role
The National Cyber Security Centre (NCSC) is the National Technical Authority, providing technical support and guidance for organisations affected by the directive. These include the development of cyber security principles for securing essential services and supporting guidance.
Support to CAs includes implementation guidance for adapting the NCSC principles for specific sector use, creating a cyber assessment framework (launched 30 April 2018), with indicators of good practice, and assisting with its use and interpreting results. The NCSC does not have a regulatory role.
The NCSC will also undertake member state obligations; these include providing a computer security incident response team (CSIRT), being the single point of contact for European partners and information sharing.
Competency and capacity
Competency and capacity preparation and development for OES and CAs will be challenging, particularly where OT security is concerned. Operational technology requires different skills to IT systems, with an engineering focus.
Critical infrastructure security practitioners appreciate the scarcity of specific skills, and suitable experience. The proposed EU Cybersecurity Act (Article 4), sets ENISA objectives for skills and competency development, certification and becoming a centre of expertise on cyber security.
Many organisations will not have the resources to prioritise security swiftly, or fully integrated cyber security governance and operations with engineering functions. Therefore, technical training, education and senior leadership awareness-raising programmes are needed. Competent authorities will need to rapidly develop or acquire cyber security capability, and auditing expertise.
Demonstrating compliance
Organisations should review the Directive requirements and guidance available from NCSC5. The principles are acknowledged good practice, and define a set of top-level outcomes, which describe good cyber security.
The NCSC has referenced existing guidance, which aligns with established cyber security frameworks. However, their application will need to extend beyond traditional information systems to operational technologies (OT).
Organisations will need to utilise and potentially source a combination of engineering and OT security expertise. An assessment of internal processes against the Directive, NCSC guidance and emerging CA requirements is recommended. Organisations will need to address areas for improvement and demonstrate how their cyber security programmes meet the Directive requirements.
Competent authorities will seek to work collaboratively with OES. CAs are encouraged to take a cautious approach to enforcement during the first year according to the DCMS Guidance for CAs. Their initial focus will be on developing a detailed understanding of security within their sector and working with operators to assess areas for further development.
However, in the industry consultation, the government emphasised competent authorities will have the power to issue penalties in the first year, should significant compliance issues arise and organisations have not made efforts to remedy them.
Applying guidance and standards
There is a proliferation of guidance which can assist with meeting the objectives of the NIS Directive. However, standards do not necessarily align well, and will not individually provide adequate coverage, hence the NCSC guidance refers to a broad collection of existing good practice. Some guidance and its application will be less familiar to some, including operational technology cyber security.
The NCSC intent is not to produce an all-encompassing cyber security compliance check list. The approach requires organisations to be capable of taking informed, balanced decisions about how they achieve the outcomes specified by the principles. NCSC expectation is for operators of essential services to:
- Understand the principles and why they are important. Interpret the principles for the organisation.
- Compare the outcomes described in the principles to the organisation’s current practices. Use the guidance to inform the comparison.
- Identify shortcomings. Understand the seriousness of shortcomings using organisational context and prioritise.
- Implement prioritised remediation. Use the guidance to inform remediation activities.
The NCSC guidance has deliberate similarities with the US National Institute of Standards and Technology (NIST) Cyber Security Framework, including referring to good practice or standards. Both contain recognised industry cyber security frameworks such as the ISO/IEC 27001/27002 standard series and for OT, the IEC 62443 series.
Self-assessment and prioritising improvements
The cyber assessment framework (CAF) has been developed by NCSC to support the NIS Directive. It will assist organisations to perform their own assessments against the NIS Directive objectives and principles, enabling the identification of effective cyber security improvement activities. The CAF fulfils an obvious omission from the NIS Directive, with the absence of a cyber maturity framework.
The CAF utilises a red, amber, green (RAG) methodology with indicators of good practice. It is intentionally less complex than other cyber security maturity models. Simplicity in application, however, will emphasise the interpretation of results, which could be challenging initially. OES may encounter difficulties showing tangible or continuous improvement for investment justification.
Supply chain management
Operators of essential services will have the responsibility to manage compliance in their supply chain. This will impact procurement of third party services, and systems/components, to ensure the security principles are applied.
OES should assess their approach to security lifecycle management, including specifying (non-functional) cyber security requirements in their contracts, and subcontracts. Suppliers will not be expected to have a direct compliance obligation according to the DCMS consultation, but, they are likely to be contractually obliged to comply.
Operators of essential services and suppliers will benefit from working towards a common set of security expectations. This will be facilitated by using a common procurement language and guidelines to ensure security objectives are integrated into systems and services.
Procurement specifications should cover all aspects of cyber security, including acceptance testing, verification, integration, maintenance guidance and any supporting references (guidelines, regulation or standards). Supply chain cyber security features in the NCSC guidance, and in recent OT standards, including the IEC 62443 series.
Onus on boards to manage risk and apply judgement
The government’s commitment to an outcome-based approach places the onus upon company boards to manage risk and apply suitable judgement. Combining an outcome focus with risk management and cyber maturity assessment will provide greater business resilience and benefits over chasing compliance.
Implementation experiences demonstrate improved risk understanding, identifying strengths and areas for improvement, informed risk tolerance and prioritising security remediation, whilst setting security budgets.
Boards will need to assess their readiness and capability to demonstrate their cyber security programmes, and implement the NIS Directive security objectives and NCSC principles. These include providing proportionate risk prevention measures, and mechanisms to detect and deal with breaches, report incidents and maintain service resilience.
Evidence of cyber security capability and practices to protect essential services will be necessary to avoid potential non-compliance. The NIS Directive and the UK regulations will concentrate board members’ attention on cyber security and resilience, highlighting the requirement to exercise good judgment where critical services are reliant upon networks, information systems and operational technologies.












